Central Key Management
RPA SaaS Admin module offers centralized key management to system administrator with secure and versatile system. In RPA SaaS Central Key Management, Key and Passphrase combination is used for application credential encryption. By default, this Salt-Passphrase is stored in product database.
As per default security configuration, the permitted settings to form a key and a salt are:
- Minimum of 32 and maximum of 128 characters
- Combination of lower case (a-z) alphabets, upper case (A-Z) alphabets and numeric keys (0-9)
|
NOTE: |
|
Accessing Central Key Management
Salt and key configured in the Central Key tab are used for credential cryptography for all sign-in applications in default tenant setup and Salt and key configured in the Global Central Key tab are used for credential cryptography for all global credentials.
Changes made to these screens are global in nature and are to be done post careful planning and considerations as mentioned in the product documentation. .
To access the central key management:
- Launch Central Key Management.
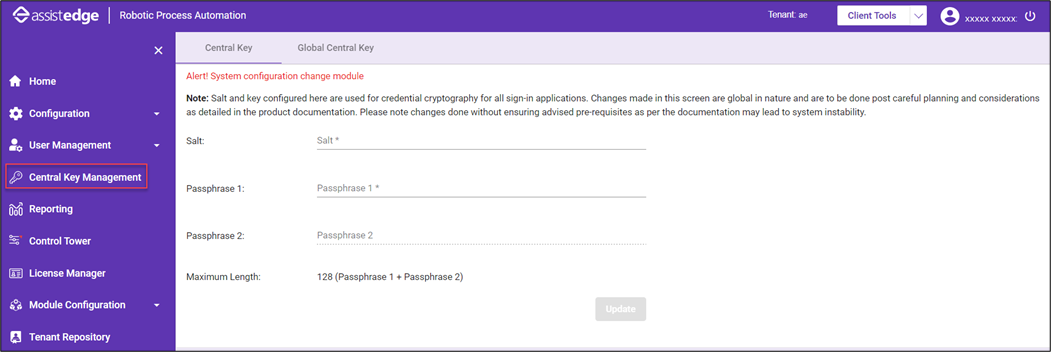
The Central Key Management system page is displayed.
|
NOTE: |
To access the Global Central Key system page click Global Central Key tab. |
- In the Salt field, enter the salt value.
- In the Passphrase 1 field, enter the passphrase 1 value.
- In the Passphrase 2 field, enter the passphrase 2 value. Passphrase 2(Secondary key) is optional.
- Click Update to save the combination into the defined store.
The credentials are updated simultaneously. For security reasons, the existing key is not displayed on the screen. Only, an update operation is permitted. The credentials are updated into the defined store.