Central Key Management
RPA Admin Module offers centralized key management to system administrator with secure and versatile system. It enables easy automation of key, generation of certificate and distribution to any endpoint. In RPA, Central Key Management, Key and Passphrase combination is used for application credential encryption. Salt-Passphrase combination is configured as a database by default. It is extended to read values from a JSON file or via Custom JS file API call.
The setting for Key and Salt length are defined in config.yml file of API framework. You can modify these values depending upon the business requirement. You are required to update the values at both API and UI end and also ensure that this settings are same at both the ends i.e., API and UI.
- For API, modify the key length in config.yml file
- For UI, modify the key length in config.json file
For more information about the detailed steps , see Customizing Cryptography section in AE-RPA- Customization Guide. As per default security configuration, the permitted settings to form a key and a salt are:
- Minimum of 32 and maximum of 128 characters
- Combination of lower case (a-z) alphabets, upper case (A-Z) alphabets and numeric keys (0-9)
|
NOTE: |
By default, only Super_Admin has access to Central Key Management page. For more information about role access, see specify role access section. |
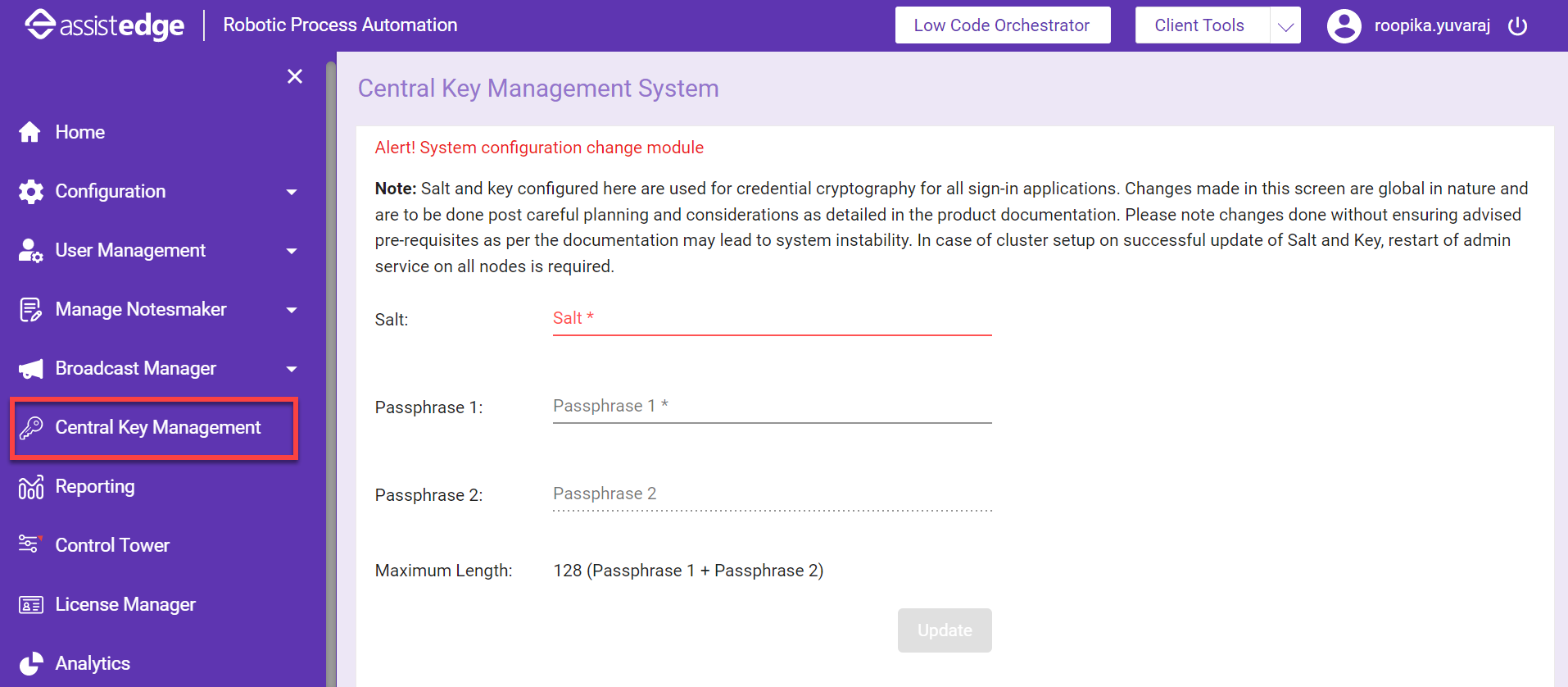
Accessing Central Key Management
Salt and key configured here are used for credential cryptography for all sign-in applications. Changes made in this screen are global in nature and are to be done post careful planning and considerations as mentioned in the product documentation. In case of cluster setup on successful update of Salt and Key, restart of admin service on all nodes is required.
To access the central key management:
- Launch Central Key Management.
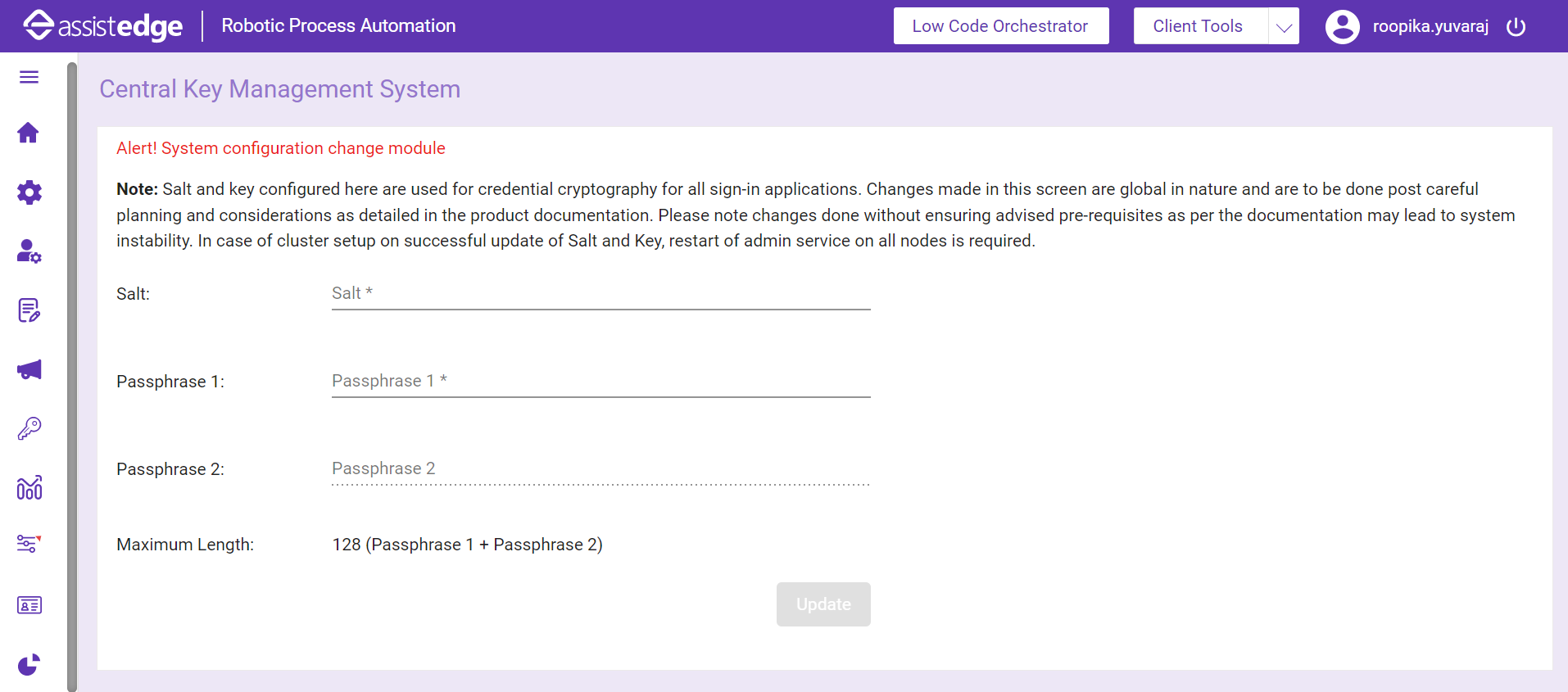
The Central Key Management system page is displayed.
- In the Salt field, enter the salt value.
- In the Passphrase 1 field, enter the passphrase 1 value.
- In the Passphrase 2 field, enter the passphrase 2 value. Passphrase 2(Secondary key) is optional.
- Click Update to save the combination into the defined store (DB, JSON File, and Custom JS file). The credentials are updated simultaneously. For security reasons, the existing key is not displayed on the screen. Only, an update operation is permitted. The credentials are updated into the defined store such as DB/JSON File/Custom JS File.