Cryptography Activity
In certain automations, before there is a transfer of sensitive data or file from one application to another, there is a requirement of encrypting that data or file.
The Cryptography Activity enables you to encrypt or decrypt text or files with the help of specified algorithms, key, and encoding. This activity also enables the hashing of text or files.
This activity supports .txt, .config, and .log type of files.
Using Cryptography Activity
- Create a new process.
- In the Canvas Tools pane, click Process Components to expand the tool and view the associated activities.
- Drag the Cryptography Activity and drop on to the Flowchart designer on the Canvas.
Output argument is automatically created to store relevant output, post workflow execution. - The instructions related to cryptography activity differs depending upon the action selected.
Click the appropriate link to know the details.
- Encrypt text– Encrypts specified text
- Encrypt file – Encrypts content in a specified file
- Decrypt text – Decrypts specified text
- Decrypt file – Decrypts content in specified file
- Hash text – Hashes the specified text
- Hash file – Hashes content in specified file
- Hash text with key – Hashes the specified text with a key
- Hash file with key - Hashes the content in the file with a key
- Configure the above steps specific to the required action and save the process.
- Click Test Run if you want to test run the process to verify the desired output.
Post execution, the relevant output is created.
For more information regarding test run, setting up environment, debugging a process, see Process Management.
Following are the supported character encoding standards:
|
Unicode |
Description |
| Unicode (UTF-8) | 8-bit UCS/Unicode Transformation Format) |
| Unicode | IT standard for consistent encoding representation |
| US-ASCII | American Standard Code for Information Interchange |
| Unicode (UTF-7) | 7-bit Unicode Transformation Format |
| Unicode (UTF-32) | 32-bit Unicode Transformation Format |
| Unicode (Big-Endian) | Storing most significant byte in the smallest address |
.
Following are the key length specifications for the algorithms:
| Algorithm |
Bits |
Key 1 (examples) | Key 2 (examples) | Key 3 (examples) |
| AES | Key length 128, 192, or 256 bits | 128 Bits : KaPdSgVkYp3s6v9y | 192 Bits : H+MbQeThWmZq4t6w9z$C&Fi( | 256 Bits: jhd(G+KbPeShV8&djp2jd)84%ep{rs8s |
| DES | Key length 64 bits | 64 Bits : KaPdSgV |
||
| RC2x | Key length 40 bits to 128 bits | 40 Bits : s5v8x |
128 Bits : 4u7x!A%D*G-KaPdS |
|
| Rijndael | Key length 128, 192, or 256 bits | 128 Bits : cRfUjXn2r5u7x!A% | 192 Bits : G-KaPdSgVkYp3s6v9y$B&E)H |
256 Bits: RgUkXp2s5v8x/A?D(G+KbPeShV8&djp2 |
| TripleDES | Key length 192 bits | 192 Bits : hWmZq4t7w9z$C&F)J@NcRfUj |
||
Using Encrypt Text Action
- From the Action dropdown list, select Encrypt text.
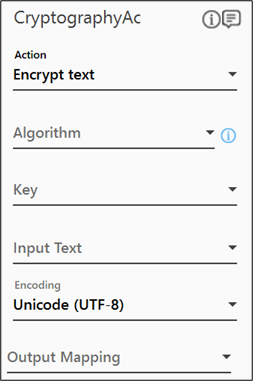
- From the Algorithm dropdown list, select the algorithm as per your business requirement.

- Define all the input parameters as In arguments and output parameters as Out arguments in the Argument bar to make it available for the selection.
- From the Key dropdown list, select the In argument holding the required key value. The selected argument must be of the String type. Refer the key length specifications of algorithms.
NOTE:
If the key length is not valid, per the selected algorithm, an error message is displayed post the process workflow execution. - From the Input Text dropdown list, select the In argument holding the required text you want to encrypt. The selected argument must be of the String type.
- From the Encoding dropdown list, select the required character encoding standard.
- From the Output Mapping dropdown list, select the required String type Output parameter. For more information see Using Cryptography Activity.
The Encrypt text action is configured.
Using Encrypt File Action
- From the Action dropdown list, select Encrypt file.
- From the Algorithm dropdown list, select the algorithm as per your business requirement.
- Define all the input parameters as In arguments and output parameters as Out arguments in the Argument bar to make it available for the selection.
- From the Key dropdown list, select the In argument holding the required key value. The selected argument must be of the String type. Refer the key length specifications of algorithms.
NOTE:
If the key length is not valid, per the selected algorithm, an error message is displayed post the process workflow execution. - From the File Path dropdown list, select the In argument holding the required file path, along with file name and its extension. The selected argument must be of the String type.
NOTE:
The file size should not exceed 8MB. - From the Encoding dropdown list, select the required character encoding standard.
- From the Output Mapping dropdown list, select the required String type Output parameter to map the status of the operation performed. For more information, see Using Cryptography Activity.
The Encrypt file action is configured.
Using Decrypt Text Action
- From the Action dropdown list, select Decrypt text.
- From the Algorithm dropdown list, select the algorithm as per your business requirement.

- Define all the input parameters as In arguments and output parameters as Out arguments in the Argument bar to make it available for the selection.
- From the Key dropdown list, select the same key value you selected at the time of encrypting the text. Refer the key length specifications of algorithms.
NOTE:
If the key length is not valid, per the selected algorithm, an error message is displayed post the process workflow execution. - From the Input Text dropdown list, select the In argument holding the required text you want to decrypt. The selected argument must be of the String type.
- From the Encoding dropdown list, select the same encoding value you selected at the time of encrypting the text. Refer the character encoding standards.
- From the Output Mapping dropdown list, select the required String type Output parameter. For more information see Using Cryptography Activity.
The Decrypt text action is configured.
Using Decrypt File Action
- From the Action dropdown list, select Decrypt file.
- From the Algorithm dropdown list, select the algorithm as per your business requirement.
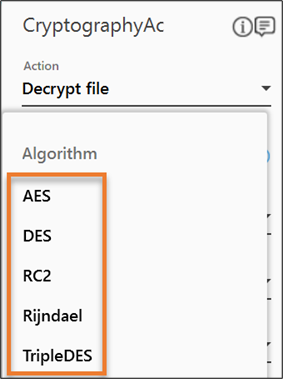
- Define all the input parameters as In arguments and output parameters as Out arguments in the Argument bar to make it available for the selection.
- From the Key dropdown list, select the same key value you selected at the time of encrypting the file. The selected argument must be of the String type. Refer the key length specifications of algorithms.
NOTE:
If the key length is not valid, per the selected algorithm, an error message is displayed post the process workflow execution. - From the File Path dropdown list, select the In argument holding the required file path, along with file name and its extension. The selected argument must be of the String type.
NOTE:
The file size should not exceed 8MB. - From the Encoding dropdown list, select same encoding value you selected at the time of encrypting the file. Refer the character encoding standards.
- From the Output Mapping dropdown list, select the required String type Output parameter to map the status of the operation performed. For more information see Using Cryptography Activity.
The Decrypt file action is configured.
Using Hash Text Action
- From the Action dropdown list, select Hash text.
- From the Algorithm dropdown list, select the algorithm as per your business requirement.
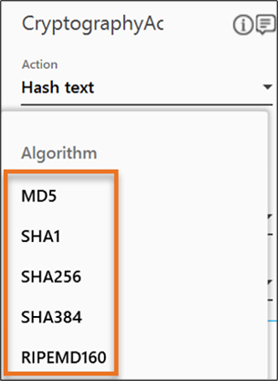
- Define all the input parameters as In arguments and output parameters as Out arguments in the Argument bar to make it available for the selection.
- From the Input Text dropdown list, select the In argument holding the required text you want to hash. The selected argument must be of the String type.
- From the Encoding dropdown list, select the required character encoding standard.
- From the Output Mapping dropdown list, select the required String type Output parameter. For more information see Using Cryptography Activity.
The Hash text action is configured.
Using Hash File Action
- From the Action dropdown list, select Hash file.
- From the Algorithm dropdown list, select the algorithm as per your business requirement.
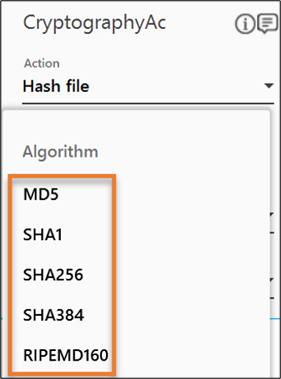
- Define all the input parameters as In arguments and output parameters as Out arguments in the Argument bar to make it available for the selection.
- From the File Path dropdown list, select the In argument holding the required file path, along with file name and its extension. The selected argument must be of the String type.
NOTE:
The file size should not exceed 8MB. - From the Encoding dropdown list, select the required character encoding standard.
- From the Output Mapping dropdown list, select the required String type Output parameter to map the status of the operation performed. For more information see Using Cryptography Activity.
The Hash file action is configured.
Using Hash Text With Key Action
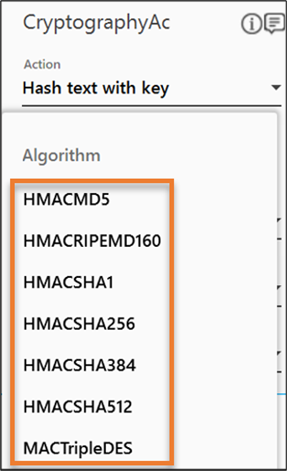
- From the Action dropdown list, select Hash text with key.
- From the Algorithm dropdown list, select the algorithm as per your business requirement.
- Define all the input parameters as In arguments and output parameters as Out arguments in the Argument bar to make it available for the selection.
- From the Key dropdown list, select the In argument holding the required key value. The selected argument must be of the String type.
- From the Input Text dropdown list, select the In argument holding the required text you want to hash. The selected argument must be of the String type.
- From the Encoding dropdown list, select the required character encoding standard.
- From the Output Mapping dropdown list, select the required String type Output parameter. For more information see Using Cryptography Activity.
The Hash text with key action is configured.
Using Hash File With Key Action
- From the Action dropdown list, select Hash file with key.
- From the Algorithm dropdown list, select the algorithm as per your business requirement.
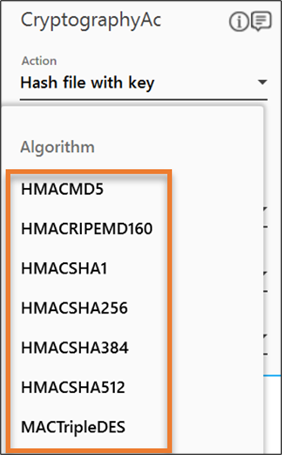
- Define all the input parameters as In arguments and output parameters as Out arguments in the Argument bar to make it available for the selection.
- From the Key dropdown list, select the In argument holding the required key value. The selected argument must be of the String type.
- From the File Path dropdown list, select the In argument holding the required file path, along with file name and its extension. The selected argument must be of the String type.
NOTE:
The file size should not exceed 8MB. - From the Encoding dropdown list, select the required character encoding standard.
- From the Output Mapping dropdown list, select the required String type Output parameter to map the status of the operation performed. For more information see Using Cryptography Activity.
The Hash file with key action is configured.
Cryptography Activity Properties
The properties of Cryptography Activity activity are listed in the following table and can be edited in the Properties grid on the right pane.
|
Property Name |
Usage |
|
Control Execution |
|
|
Ignore Error |
When this option is set to Yes, the application ignores any error while executing the activity. If set to NA, it bypasses the exception (if any) to let the automation flow continue; however, it marks the automation status as failure, in case of an exception. By default, this option is set to No. |
|
Delay |
|
|
Wait After (ms) |
Specify the time delay that must occur after the activity is executed. The value must be in milliseconds. |
|
Wait Before (ms) |
Specify the time delay that must occur before the activity is executed. The value must be in milliseconds. |
|
Misc |
|
|
Breakpoint |
Select this option to mark this activity as the pause point while debugging the process. At this point, the process freezes during execution allowing you to examine if the process is functioning as expected. In large or complex processes, breakpoints help in identifying the error, if any. |
|
Commented |
Select this option to mark this activity as inactive in the entire process. When an activity is commented, it is ignored during the process execution. |
|
DisplayName |
The display name of the activity in the flowchart designer area. By default, the name is set as Cryptography Activity. You can change the name as required. |